Why is vulnerability management so important?
There are both intrinsic and extrinsic incentives to manage your software vulnerabilities properly. The intrinsic bottom line is that there are severe economic and reputational consequences for companies that fail to identify their software vulnerabilities and respond to them effectively.
Added to this are extrinsic factors such as industry best practices and a growing number of regulations requiring organisations processing sensitive data to implement risk-based vulnerability management.
So do we simply evaluate and buy the best vulnerability scanning software?
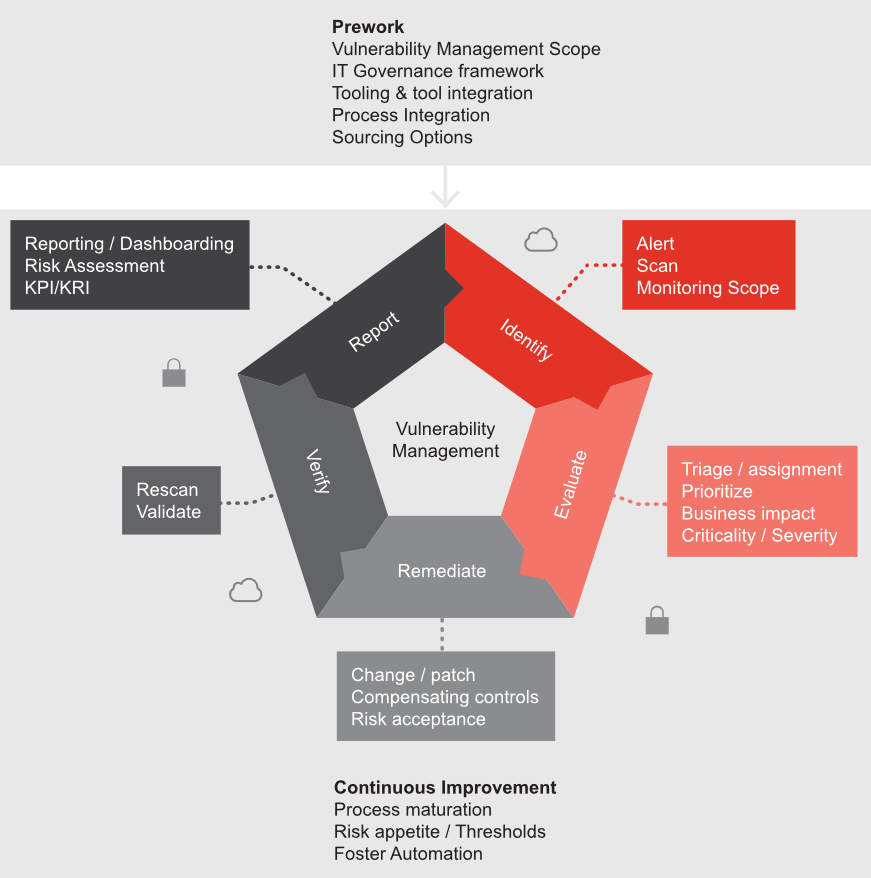
It’s important not to confuse vulnerability management with merely assessing or scanning for vulnerabilities. Vulnerability management isn’t just an aspect of IT hygiene. It’s an essential part of IT risk and compliance management, and key to establishing and maintaining trust in IT services. It also has to be seen as a cycle rather than just a static building block of your processes.
In the white paper we see how it’s possible to make vulnerability management an integral part of your IT governance framework to achieve a sustainable and mature security level by proactively identifying and remediating vulnerabilities, while at the same time complying with ever-increasing regulatory requirements.
What is vulnerability management?
Vulnerabilities are bugs that can be exploited by people with malicious intent to circumvent security controls and gain access to your systems and data.
The aim of vulnerability management is to identify and remediate known vulnerabilities and assess how able and mature your IT organisation is when it comes to applying security patches within a defined time objective. Vulnerability management is an ongoing process of identifying, evaluating, remediating, verifying and reporting vulnerabilities in IT systems and the software which runs on the IT infrastructure.