Closing the gap between cybersecurity specialists and the board
85% of CEOs referred to the rising complexity of cyber risks as a major concern, according to PwC’s 2020 Global CEO Study. Spending on cybersecurity is predicted to increase globally to USD 133.7 billion in 2022, a compound average growth rate of 9.2% a year. As a result, cybersecurity has moved from being an additional task given to the IT department, to one that is regularly covered at Board level. Despite the recognition based on financials, it is not necessarily well-understood because Chief Information Security Officers (CSIOs) and Board members often speak different languages. CSIOs speak about threats in technical terms such as phishing, breaches, malware and ransomware. Board members want to understand the language of business – risk, opportunity cost, and “bottom line” impact. As a result, cybersecurity investments may be declined or not optimally aligned with business objectives.
Closing the gap between these two perspectives has considerable advantages including:
- Cybersecurity is more likely to be seen as a business investment, and one which can convey a competitive advantage, rather than a cost factor.
- CSIOs earn the trust of their boards and are welcome to talk to the board regularly.
- The number of time-consuming ad hoc requests from boards is significantly reduced.
- Customer trust in the business is likely to be enhanced, along with business sustainability.
Four key steps to closing the gap
CSIOs can close this translational gap by taking four key steps:
1. Prove the value of the investment and how you will manage and mitigate the risk
2. Benchmark performance, transfer and communicate successes
3. Implement and report on continuous cybersecurity awareness and readiness campaigns
4. Appoint someone with whom board members can address any cybersecurity issue, any time
1. Prove the value of the investment and how you will manage and mitigate the risk
CSIOs need to prove the value of cybersecurity and any major budget item in investment terms. Board members receive many technical reports. Although technically correct, such reports do not always make sense to board members due to the level of complexity. In addition, as the results are not presented in clear business terms, the required actions and the effect of not doing them are not clear to them.
Presenting your case in investment terms means that boards can compare them against the other investment options they are asked to approve. At a high level, this means showing the likely return on investment. For example, if a cybersecurity issue, such as a breach, is likely to cost CHF 4.0 million and requires an investment of CHF 1.0 million to reduce the risk by 45%, then the initiative has a potential return of 35% which can be compared against other potential investments.
Boards expect their ICT partners to identify the types of risks associated with each case and how they will manage them. This typically involves scenario analyses. For example, is it a reputational risk where customers’ data has been obtained and trust and revenues lost? Is there a risk of a regulatory penalty, for example, under the General Data Protection Regulation (“GDPR”)? Who are the likely attackers – state agents, organised crime or individual hackers? What are the best forms of risk mitigation and why?
The good news is that there are many services available to help you quantify and compare the risks, associated business impacts as well as risk mitigation options and costs. The following examples provide overviews of cyber risk scoring and impact analysis.
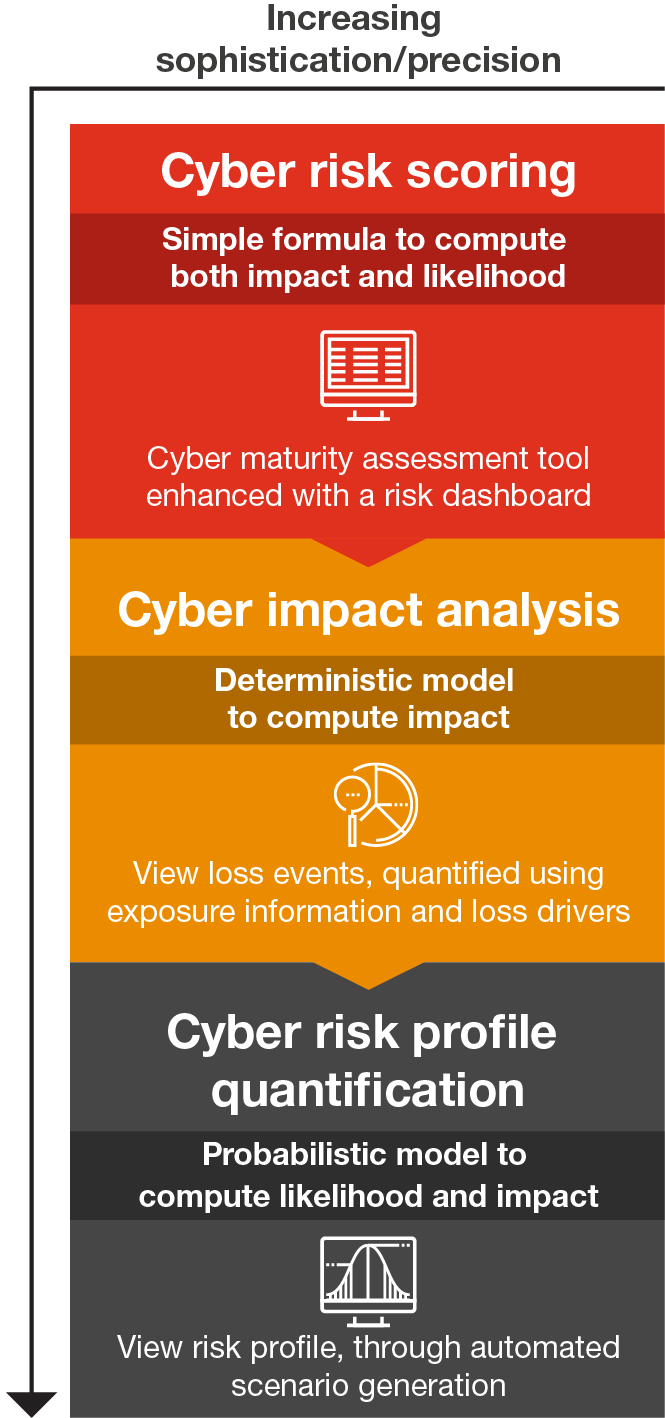
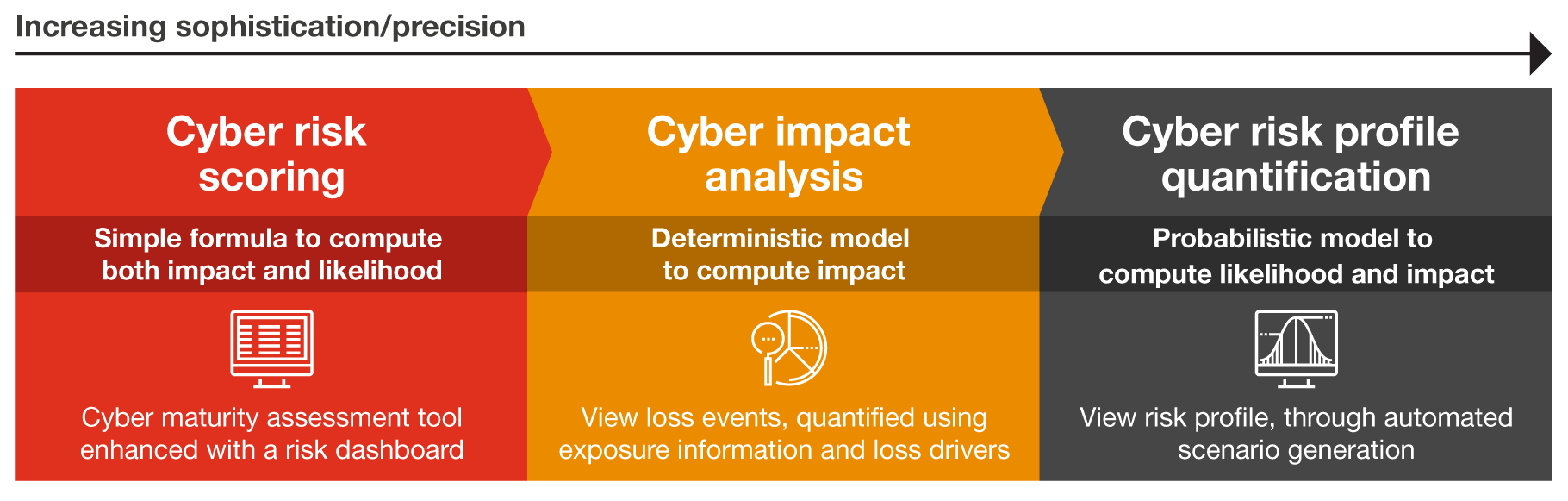
In addition, the insurance industry has developed many cybersecurity valuation approaches in order to insure against cyber-related losses. These provide useful insights for CISOs in addressing key risks.
2. Benchmark performance, transfer and communicate successes
Boards typically expect internal and external benchmarks. Regular questions include: Is our cybersecurity performance improving? Is this enough? How do we compare against other industry players?
You should base your assessment on a standardised and well-proven framework, such as the Swiss ICT minimal standard (based on the NIST cybersecurity framework) or similar. The Swiss ICT minimum standard covers a range of topics from identification, protection, detection, to reaction and recovery.
Based on cybersecurity risk maturity assessments we typically work with organisations to measure and communicate the success of these factors at board level.
Cybersecurity is an industry-wide topic. For this reason, we also encourage and host industry based CSIO round tables such as the Swiss Cyber Expert Group. This enables cybersecurity experts to discuss what has worked for them, what has been less successful and why. It also enables them to transfer the learnings and successes across organisations (insert link to next such event if available).
3. Implement and report on Continuous Cybersecurity Awareness and Readiness Campaigns
Physical infrastructures such as roads and public transport, have been around for over a century. As a result, people are familiar with the safety rules such as stopping at a red light. In comparison, the digital infrastructure is approximately 25 years old and has developed at a much faster rate. For these reasons, people are less likely to understand the risks, for example, of opening phishing emails with attachments that request sensitive information.
Even with physical infrastructure, rules need reinforcement such as adding the protection of lights at some pedestrian crossings. Similarly, we not only need to ensure that all employees understand key cybersecurity threats, but that they are supported by processes and systems to encourage the correct behavior. For example, cyber threat readiness training using simulations has proven extremely effective in raising the cybersecurity awareness and readiness of many companies. In addition, companies such as PEP Security offer end point and in-transit email encryption with the added reinforcement of traffic light-based icons. A red “traffic light” reminds recipients not to open the email under any circumstance.
4. Appoint someone with whom Board Members can address any ICT or Cybersecurity Issue, anytime
Being prepared for regular board meetings to discuss issues in business terms is critical. Having someone with whom board members feel comfortable discussing ICT and cybersecurity issues is just as important. Based on our experience, boards are interested in having such a “go to” person regardless of where they sit in an organisation. The discussion about who that person reports to (e.g. the CIO, CRO, COO or CFO) is not a priority issue for them.
Start Now:
If you haven’t already done so, nominating such a “go to” person is the best place to start.






